For years, we have used passwords to protect our security. We used different kinds of passwords. From mechanical locks and keys to digital ones and of course current passwords for our accounts.
Setting passwords helped us to secure our accounts but as we had progress in safe passwords, others made progress to break them. For years, we protected our accounts and goods against humans but what we’re facing now is computers.
We’ve been trained to set passwords hard to remember for humans but easy for computers to find. This should be changed.
Passwords vs. Passphrases
Most people set passwords for their accounts; which is a weak practice. Passwords are weak and easy to find. As I said, we’re not facing humans now, we’re facing computers. Many people think passwords can protect them against crackers but setting a easy-to-remember password is not how most people get cracked.
Most crackers use databases of passwords to attack people. They have a database of usernames and a database of passwords and they try to match an account to a password. They can test a million accounts in just few seconds until they find a match.
Now if your service provider doesn’t encrypt (hash) your passwords, they can easily find your password and use it to access your different accounts.
What most people use is password. There’s not a lot of people who use passphrases. A passphrase is a combination of (pass)words, possibly with spaces, special characters, and numbers. While 1LoveMyHorse is a password, “2%horse &a human 3mushrooms – not a rabbit” is a passphrase. What we should focus on is the randomness and the number of possible states for guessing phrases.
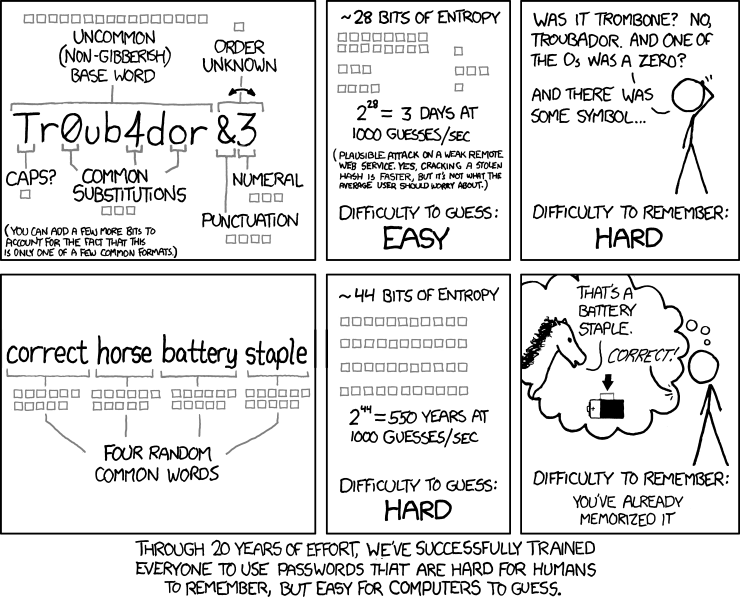
An account can be compromised with a brute-force attack but you can be safe with a passphrase. There’s not any account that can be safe completely or ever but it’s the matter of time. A password like “CerealBox” takes only a second to be compromised.
However, a passphrase like “Friend$Purify$Commute7$Wildness$Lustfully$Snowiness” can take a million years to break. You can also be safe with a password like “X35@2sd1r$90e%&V57#06%&TWaz&z93#” but remembering a passphrase would be much easier.
AviD’s rule of usability
XKCD assumes the attacker knows the user has generated a passphrase by choosing four of the most common (top 2,048 in this example) dictionary words at random. Even so, the passphrase contains more entropy than the password. There are only 94 possible options for each password character, meaning, less uncertainty. So, mathematically speaking, a passphrase could be more secure.
But XKCD’s argument is not primarily about mathematics. It’s about how to create the most secure systems possible in light of human imperfections.
For decades, the advice from information security experts was to change your passwords frequently and use numbers, capitals, and special characters. But we humans are bad at creating randomness, and we’re bad at remembering things. So inevitably people used simple words, names, birthdates, and sayings, swapping out letters with similar-looking special characters. Crackers can crack these kinds of passwords in a matter of seconds.
In an effort to make secure systems, the prevailing password advice actually made the systems less secure. Or, as the user AviD now-famously put it on Stack Exchange, responding to the XKCD comic: “Security at the expense of usability comes at the expense of security.” In other words, if your “secure system” isn’t easy to use, people won’t use it, negating the security benefit.
How long should a password be?
There are multiple elements to make sure a password or a passphrase is safe enough. For years, security specialists told us that a good password contains uppercase and lowercase words, numbers, and special characters (#$%& etc.).
First, we should find out about the ways our accounts or passwords can be compromised.
Ways to crack a password
First, you should understand something about how crackers steal passwords. Bad guys typically begin trying to crack a password by using a dictionary attack. A dictionary attack works by drawing on a massive database of dictionary words, real passwords exposed in previous data breaches, names, as well as common combinations (such as last name + first name + date) and substitutions (like “@” instead of “a”). To get an idea of what kind of data crackers can glean from a password leak, check out this report.
If a dictionary attack fails, the cracker will have to use a brute force attack. This type of attack is much slower because it means the computer will go through every possible combination of characters, one by one. Some computers can guess hundreds of billions of passwords per second.
Keep in mind, crackers generally are not trying to guess your password at the login page of your online account. Instead, they will usually attempt dictionary or brute force attacks on a database of hashed passwords stolen from a company’s servers. There are various ways companies can hash passwords to bog down the process for crackers, which can help keep your plaintext password secure. But it’s better to create a strong password yourself rather than place all your trust in the cybersecurity practices of a website.
How to prevent brute force attack
There are two ways to make it more difficult for someone to brute force your password: make your password longer (by using more characters), and make it more complex (by using a greater variety of character types, like numbers and capital letters). Note, however, that length is much more effective than complexity at preventing a brute force attack.
Every additional character in a password increases the length of time it would take a supercomputer to guess your password by an order of magnitude, even if you only use lower-case letters. Adding complexity also helps because it will broaden the set of characters the computer has to check, but not by nearly as much.
There are online calculators that claim to tell you how long it would take a computer to crack your password. These are not precise because of all the variables involved, such as computing power and the hash used. But they can serve to illustrate a key point about password length: a six-character random-generated password using a mix of character types would take seconds to crack, whereas a 10-character password with only lower-case letters could take several years.
Why a long password isn’t always better
Brute force attacks are not very efficient and can be easily thwarted by merely creating a longer password. That’s why dictionary attacks are a more efficient way to crack passwords. Dictionary attacks take advantage of human weaknesses, like predictability and poor memory. The need to remember passwords leads users to choose simple passwords, which are also easy to guess.
With dictionary attacks, therefore, length can be a misleading measure of password strength. For example, “F3rnand3zJ@nu@ry1983” looks like it could be a very strong password because it contains lots of numbers, capital letters, and special characters. But this password would probably be cracked in a dictionary attack: It’s just a last name, a month, and a year. The algorithm could easily look for predictable character substitutions and capitals.
How long should your password be?
The length of your password primarily depends on whether you’re using a password with random characters or one with a series of words.
If you want to create a strong password using a series of words (a “passphrase”), most info security firms recommend using at least four words that aren’t very common. As more people switch to passphrases, however, crackers will get better at cracking them.
If you’re using a password composed of random characters, about 15 should put it out of reach of modern computing capabilities. However, we don’t recommend using random-character passwords unless you’re using them with a password manager, which will help you generate and store them securely. That way you don’t have to remember them or write them down, and they will be unique.
If you use a password manager, we recommend using a long passphrase as your master password and generating a unique random password for each account, relying on the default settings for length and complexity (usually 20 characters, with a few numbers and special characters).
What I do
I simply use a password manager. There’s a lot of free software password managers to help you make a strong password or passphrase. Also, with a password manager, you’re not forced to remember all your passwords and accounts so you can easily create a unique strong password for each of your accounts.
Parts of this article are originally published by Proton Mail blog. You should keep the references.

